Password Protection
Root Password Protection
![]() In the manual method of installing an SSL Certificate, the Administrator must have ‘Root’ access on the server. This means that the Administrator has the unique username and password that enables access the core of the machine. As layered security is designed to protect the core of any IT asset, providing core access to multiple Administrators potentially undermines this security principle.
In the manual method of installing an SSL Certificate, the Administrator must have ‘Root’ access on the server. This means that the Administrator has the unique username and password that enables access the core of the machine. As layered security is designed to protect the core of any IT asset, providing core access to multiple Administrators potentially undermines this security principle.
Root access on any server should be a carefully guarded secret within your organisation because if this access is compromised, the entire server is vulnerable to endless security issues. Notwithstanding this fact, many organisations still store these passwords in clear text format on PCs with little, or no, real security in place.
Previous attempts to automate SSL delivery within the organisation have required Root passwords to be stored on a central server or in ‘line commands’ to be executed in the servers on the network. The central server has root access to all the servers it controls and must be able to send executable commands to those servers in order to function correctly. This requirement is a security weakness of these systems and is considered flawed.
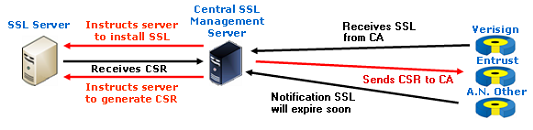
Central server SSL management has not been adopted by the more security conscious organisations simply because the requirement of this server to centrally store Root access privileges gives rise to a ‘single point of failure’ and undermines the ‘best practice’ of layered security. Security architects will advise against the practice of single-point-failure wherever possible.
In choosing to adopt the AACD™ system to automate the SSL life cycle(s) in your organisation, you will download DSSA™ software and install it on every server on the network that requires SSL Certificates. This software does not use Root access passwords to function. The fact that the Root access password is not required is an improved layer in the protection of the servers’ integrity and security.
