AACD explained
How the AACD™ Solution Works
![]() The AACD™ system is the unique SSL Management system used to assist any Certificate Administrator in completely automating the deployment and management of their Certificates. When considering AACD™, it is important to understand that while all of the life cycle issues are automated, security is improved without any disruption or negative impact to your organization.
The AACD™ system is the unique SSL Management system used to assist any Certificate Administrator in completely automating the deployment and management of their Certificates. When considering AACD™, it is important to understand that while all of the life cycle issues are automated, security is improved without any disruption or negative impact to your organization.
AACD™ is a simple solution to a simple issue. It treats the issue first as one that must improve security and then improve efficiency by automating processes. Once the security is assured by the AACD™ authentication method (and this is done automatically) then the system begins automating the SSL life cycle of every Certificate in your organization.
To secure the environment and the server(s), the AACD™ system uses a unique concept called ‘The Trust Triangle’. Once established, the Trust Triangle provides the security necessary to automate the Certificate life cycle process within your organization. This patent protected system ensures that only Authorized and Authenticated servers can request and receive Certificates.
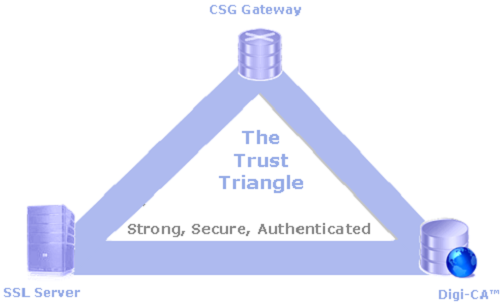
For the Trust Triangle to function correctly and securely, the Daemon or Server Side Software™ [DSSA™] must be installed on the SSL Server. This software automatically joins the SSL server to the AACD™ system to form the third component of the Trust Triangle. Once the Trust Triangle is formed, the AACD™ system is activated and automatically renews the SSL Certificates on all of the servers connected to it.
Removing the ‘Human factor’ Factor
Rather than relying on your organization Certificate Administrator(s) to renew Certificates on time, and every the time, AACD™ automates the entire process and removes the human factor too. By automating the process, the human factor that causes SSLs to expire and time lost on manually requesting and installing certificates, or waiting for the CA to deliver the Certificates, are all removed.
As stated, all of this is achieved using highly secure cryptographic technology to ensure that the layered security of your environment is improved and that it remains fully operational without interruption and without undermining its integrity.
